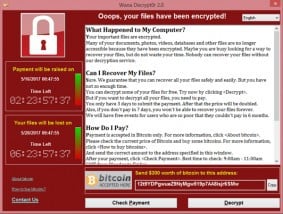
WannaCry Ransomware, All you want to know about, protect your PC
What is WannaCry or WannaCrypt?
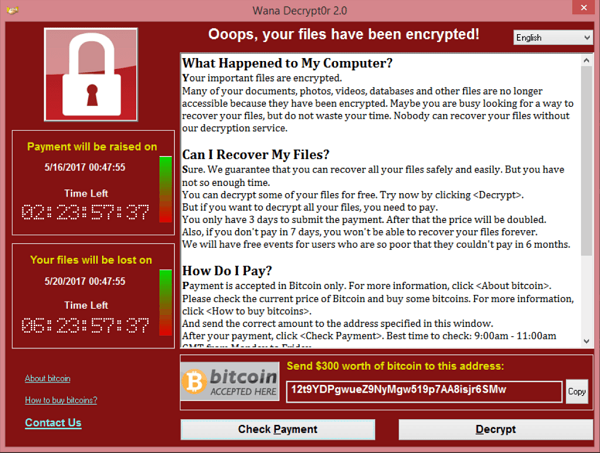
Who Developed the malware?
Nobody yet claimed or accused responsible for it.
How WannaCry was developed?
NSA developed a tool EternalBlue to hack criminal’s Windows PC using vulnerability of Microsoft Windows SMB implementation, which reportedly theft latter by a group Shadow Brokers and then lost. WannaCry is believed to be hacker’s modified implementation of EternalBlue. Source Wikipedia (link)
How it is spreading?
- From Email Attachment: The malware first came as an email attachment .docx file (Source: Internet). Fake email attachments claiming receipt of important service, online bill or any other may contain this malware. Spam email with embed link also contains the malware.
- Using SMBv1 Protocol of Microsoft Windows: The malware exploits vulnerability in Microsoft Window’s SMB (Server Message Bus Protocol) implementation, a protocol windows PC widely use for file, printer etc sharing. Once a PC is affected the malware randomly searches for other PCs over local network and infect them. Note, it’s not a fault of SMB protocol itself rather a fault of Microsoft’s implementation of it.
- Upon reaching a fresh PC the malware try to connect to two website “www[.]iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com” & “www[.]ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”. If the connection is successful the malware stops spreading. Upon an unsuccessful connection the malware infect the victim PC and start spreading. Reason of such peculiar behavior is still unknown. Source: Microsoft Blog.
Which Systems are susceptible for WannaCry attack?
Systems installed with Windows version older than Windows 10 are only susceptible for this attack. As Microsoft has already patched the security whole in Windows 10, Windows 10 is immune to it.
How Can I Immune my system to defend WannaCry?
- Install anti WannaCry patch from microsoft. Latest Windows Update installs this automatically. The easiest way is to install all Windows update in a Genuine Windows system. You can turn on Automatic Windows Update from control Panel. Or you can download the cumulative update for your required windows version from this technical blog. (link). Alternatively you may obtain the patch for your specific windows version from this (link) [Easy to follow]. Microsoft has released anti wannacry patch for old Windows versions like Windows XP, Server 2003 and Windows 8 which are otherwise unsupported.
- Never click attachments and links from any unkown or suspecious email. Don’t download anything from unknown website. Don’t participate in unknown surveys, offers etc. Website claiming to contain software cracks are very common source of malware. Remember cracking software is also illegal.
- Install a good antivirus (preferably paid internet security). I personally recommend AVG Internet security. Kaspersky, Norton or any other good antivirus is OK.
- Block incoming traffic at TCP port 445 with windows firewall or your internet security firewall.
What to do if I’m already affected?
Unfortunately very little can be done if you’re already affected. Following steps may help you.
- Please don’t pay 300 USD Bitcoin to them. There is no guarantee you’ll get your files back. Additionally this will further strengthen them to develop the malware.
- Currently no 3rd party tools available to decrypt the files for you.
- So one option is formatting your PC and restore files from back-up. Don’t connect your backup drive with affected PC. The backup drive may also become encrypted. First full format the affected PC and re install the operating system. Then follow the above mentioned steps to immune your system. After all this steps only connect your backup drive to PC and restore backup files. So, it’s always a good idea to keep an offline backup of important files.
- Alternatively you can wait for some days if any antivirus research group comes with decryption tool for WannaCry malware.
Please share this blog to increase global awareness. For any confusion or to share your observation with WannaCrypt please comment bellow. For any other help contact with the site administrator from contact us section. Thanks for reading us.
Views: 269