What is SSH Tunneling and port forwarding, Explained with Steps involved
Introduction: What is tunneling?
In networking tunneling refers passing network traffic from source to destination via some intermediate. The intermediate may be a server or a network router which acts as gateway between source and destination. Way of interaction between gateway and destination server depends on the type of actual communication. Tunneling decides how the traffic moves from source to gateway server. Technically speaking, it’s the actual protocol say http or https for web responsible for gateway to destination communication. Tunneling protocols decides way of communication between source to gateway server. Tunneling hides most of the information regarding actual client from rest of the world and save clients from several network attacks. So, nowadays it’s an famous method of setting up proxy server.
Description of terms used in this article:
- Tunneling Protocol: The protocol used for passing data from Client to Gateway.
- Communication protocol: Actual protocol, that should be used by the client in absence of any tunneling. In case of a web browsing http or https will be considered as communication protocol. Or in case of email sending it’s SMTP.
Disclaimer: This article is regarding what is SSH Tunneling and not about how to set it up. Read this and further articles to learn setting such a tunnel in Linux and Windows, and how this helps while setting a server.
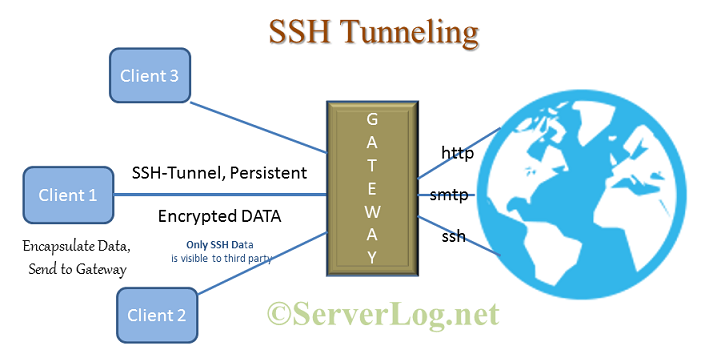
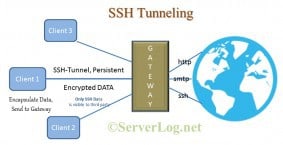
What is SSH Tunneling
As the name suggesting here the client and gateway communicate over SSH. Clint first authenticates itself to gateway server with SSH credentials and then a client-gateway SSH connection establishes. Client machine encapsulate all outgoing data with ssh header at application layer and send them to gateway server over the existing SSH. The process flow is as follows.
Steps Involved in SSH Tunneling
- Client connect with gateway over SSH and authenticate itself with SSH log in credentials.
- A SSH connection starts between client and gateway
- Client encapsulate all data (of any type) with ssh header at application layer and send it to gateway. [Note: Here client don’t re-write the destination IP address in communication packet. Instead encapsulate it with tunneling packet header and mention gateway server’s IP in that packet.]
- Gateway receive the encapsulate data and extract the communication packet data from it.
- Then Gateway decides what type of data it is, and the actual destination from communication packet header.
- Now Gateway communicate with the destination using it’s own IP address and communication protocol. [Note: Here gateway server rewrite client’s IP address with it’s own, else the response packet will not reach back to gateway.]
- Destination server responses and communicates with Gateway as it do with any other client and remain unconscious about the client. [Note: This means destination Server don’t receive any data about client from communication data packet header. Still destination may get some short of information regarding actual client from cookie or any other extra information specified in the data.]
- Gateway encapsulate the received data and pass it back to client. [Here again no IP re-write]
SSH being fully encrypted, this type of tunneling is highly secure and anonymous. No third party between Client and Gateway server can decrypt those data to gate any information regarding destination and what kind of data it is. While communicating over an insecure network say from a cyber cafe, this type of encryption gives high transmission security at client’s end.
What is SSH port forwarding?
Port forwarding is an inherent part of SSH tunneling. Over SSH it’s possible to forward all traffic reaching to a particular TCP port of a client to gateway and vice versa. This looks like a particular port of client or server is forwarded to other, so name is port forwarding. Depending on it’s nature three type of SSH port forwarding is possible viz. Local, Remote and Dynamic Port forwarding (Will be discussed in next posts). Besides setting up anonymous proxy SSH port forwarding (mainly Local and Remote) comes very handy while setting up a cheap high volume salable server.
Use of SSH Tunneling and Port Forwarding
- Setting up anonymous proxy with Dynamic port forwarding
- Easily setting up IPv6 over IPv4 even behind NAT or firewall.
- Redirecting traffic from one server to another during maintenance etc.
ServerLog thanks you for reading us. Please follow our next posts to know how to implement SSH tunneling. For any further quarry ServerLog invite your comments.
Views: 226